Encryption
Encryption is the process of taking plain text, like a text message or email, and scrambling it into an unreadable format. This helps protect the confidentiality of digital data either stored on computer systems or transmitted through a network like the internet.
Encryption can help protect data you send, receive, and store, using a device. Encryption is the process that scrambles readable text so it can only be read by the person who has the secret code, or decryption key. It helps provide data security for sensitive information.
It’s nearly impossible to do business of any kind without your personal data ending up in an organization’s networked computer system, which is why it’s important to know how to help keep that data private.
In recent years, encryption has become far more widely available on a wide range of consumer and business products and services. As a result, more data is routinely encrypted today than ever before. Today, encryption protects the communications of individuals and organizations from unsophisticated and sophisticated criminals and repressive governments. It assures the security of electronic commerce transactions over the Internet. Encrypted communication capabilities are built into major computing platforms and in an array of messaging applications that are used by hundreds of millions of users.
Symmetric and Asymmetric encryption
An encryption key is a series of numbers used to encrypt and decrypt data. Encryption keys are created with algorithms. Each key is random and unique.
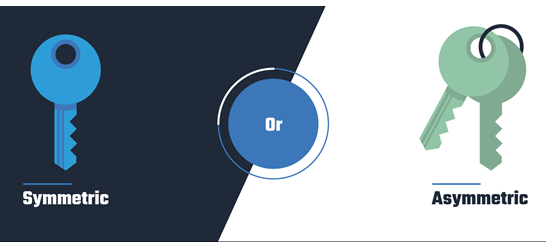
There are two types of encryption systems: symmetric encryption and asymmetric encryption. Here’s how they’re different.
- Symmetric encryption uses a single password to encrypt and decrypt data.
- Asymmetric encryption uses two keys for encryption and decryption. A public key, which is shared among users, encrypts the data. A private key, which is not shared, decrypts the data.
Computer and communications systems use cryptography for three broad purposes—to protect the confidentiality of information (i.e., encryption), to protect the integrity of information, and to authenticate the originator or sender of information. Applications that require the secrecy of large volumes of information use symmetric cryptography. Asymmetric (public key) cryptography is frequently used to securely disseminate keys that are used in symmetric cryptography.

Use Cases for Encryption
Databases
Protecting data stored in databases is a top use case across mainframes, relational, and NoSQL databases.
Cloud Storage
Encryption is the main data security control for cloud computing.
Compliance
Compliance is a principal driver of encryption and tokenization
Payments
In the payment use case, the idea is to remove payment data wherever possible
Applications
Application encryption is selected when fine-grained control is needed