
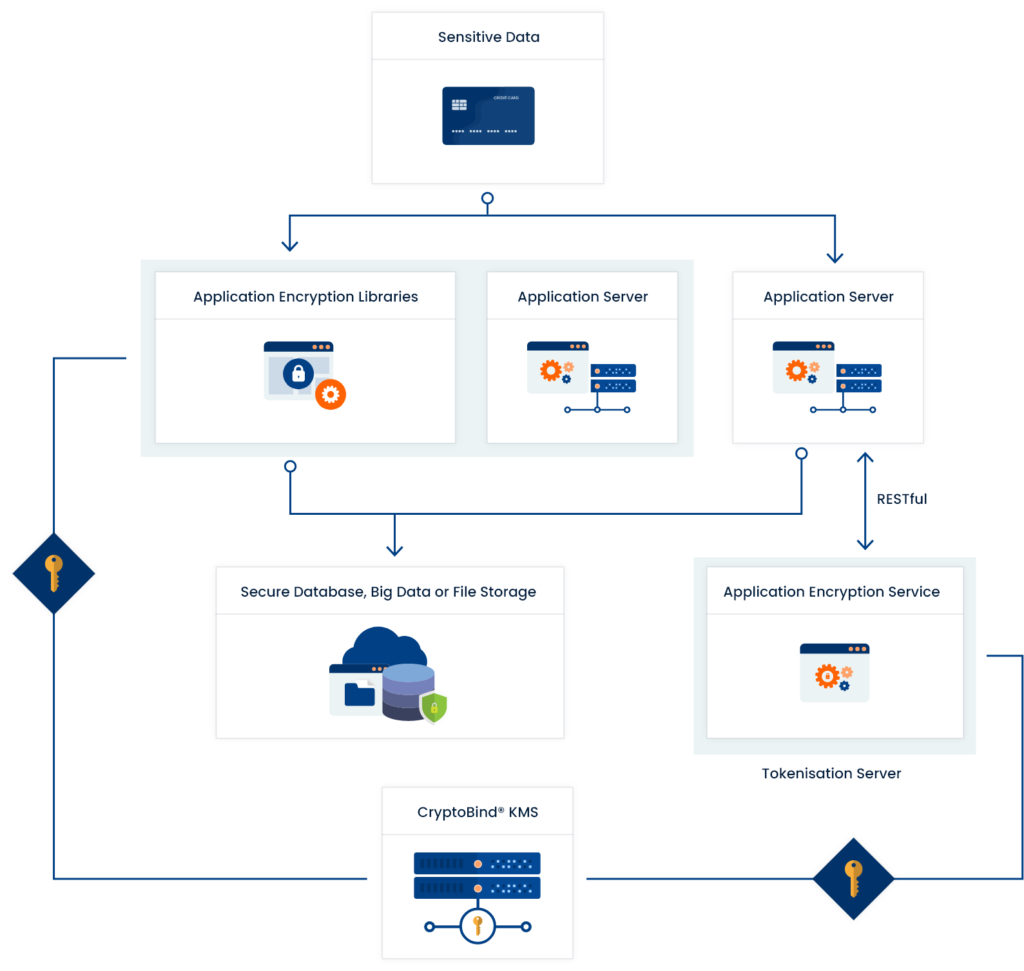
Application layer encryption is a data-security solution that encrypts nearly any type of data passing through an application. When encryption occurs at this level, data is encrypted across multiple (including database, disk or file) layers. This application layer encryption approach increases security by reducing the number of potential attack vectors. Another advantage to application encryption is that, since it encrypts specific fields at the application layer, organizations can secure sensitive data before storing it in database, big data, or cloud environments.
What is application-level encryption?
Is it related to end-to-end encryption? Client-side encryption? Field-level encryption?
Each of these terms point to a combination of data flow choices (how the data will move between components, where the encryption will happen, how the data will be used) and security guarantees (what will encryption protect against and under which set of assumptions).
The name implies that application-level encryption is implemented within your application so that sensitive data security in your application doesn’t depend on the security of transport/at rest encryption of underlying layers. ALE can be as many things as you make it:
- It can happen on clients, making it client-side encryption.
- It can happen on clients in a way that no secrets or keys are available to servers, thus making it end-to-end encrypted.
- It can be context-aware and protect certain fields, thus becoming field-level encryption.
- Its end-to-end encryption can operate under full Zero Trust assumptions, making the application compliant to zero trust architecture principles.
In short, application-level encryption only points to an architectural choice of where encryption happens
Benefits of Application-level encryption
Every security requirement should be driven by a risk model and a threat model that justifies the choice of security control, the scope of its application, and details. Application-level encryption addresses several main goals:
Trust your infrastructure less
Application-level encryption provides data protection on all underlying layers, including all layers of storage and sometimes transit. This drastically decreases the number of attack vectors on sensitive data. Outdated TLS settings or expired TLS certificates won’t lead to data leaks when the data is application-level encrypted.
Defense-in-depth
Add another layer of security if other data-related controls like underlying (disk, transit) encryption or access control fail somewhere.
Higher level of security against insider and advanced adversary risks
processing financial transactions and storing transaction data, the risks of insiders or privileged adversaries gaining access to the database are more significant. Think malicious DBA, cloud employee, an adversary with elevated privileges including developer/DBA access.
Greater agility and more control on performance and capacity impact
You can encrypt only what needs protection when you choose data to encrypt inside business logic.
Compliance
Although there is very little precision in encryption requirements in different regulations, none of them precisely says “you need to implement encryption at the application level”—using it simplifies compliance and makes implementing regulatory requirements helpful in other practical goals.
The longer sensitive data stays encrypted in its lifecycle, the closer application-level encryption gets to end-to-end encryption and zero trust architecture. The shorter data stays encrypted, the closer it gets to single point-to-point transport encryption or encryption at rest.
