Introduction
This use case has been developed for JISA’s CryptoBind HSM (Network Security Module by JISA Powered by LiquidSecurity) product. JISA’s HSM can be integrated with code signing solution. Code signing is the process of digitally signing executables and scripts to confirm the software author and guarantee that the code has not been altered or corrupted since it was signed. Code signing confirms the authenticity and originality of executables and scripts. It assures this information is valid and establishes the legitimacy of the author. Code signing process employs the use of a cryptographic hash to validate authenticity and integrity.
Definitions, Acronyms and Abbreviations
HSM : Hardware Security Module
Cryptography : Cryptography is a method of protecting information and communications through the use of codes, so that only those for whom the information is intended can read and process it.
Hash: Hashing is the procedure in which a hash function is used to convert the software code into arbitrary fixed value to represent other the code. This value is referred to as Hash.
OS: Operating System of a consumer on which software would be installed
PKI: A public key infrastructure (PKI) is a set of roles, policies, and procedures needed to create, manage, distribute, use, store and revoke digital certificates and manage public-key encryption. PKI provides “trust services” – in plain terms trusting the actions or outputs of entities, be they people or computers.
CA: In cryptography, a Certificate Authority (CA) is an entity that issues digital certificates.
Explanation of use case contents
This use case contains following contents which may be applied across a wide range of system types. This section will provide explanation for each content of the use case
Name of use case
Code Signing Solution Integrated With CryptoBind HSM
Description
Today internet is the primary medium through which software is distributed, accessed and used. The worldwide use of this medium has also introduced risk factors. Hackers and cyber criminals may obtain secured executable files and insert malware into it. As a result any user downloading and accessing this file would fall victim to the malware. Because of the potential damage that an executable or script can cause to a computer system, it is important that users be able to trust code published on the Internet. Code signing identifies that the software or application is coming from a specific source. It also ensures that a piece of code is not altered and it is trustworthy. Users are assured who they are downloading software from.
Why to use CryptoBind HSM in this use case?
In code signing environments, a critical vulnerability exists is private keys. Anyone who can access legitimate certificate owner’s private key can create software that will appear to be signed by that organization. In order to effectively secure private keys used in code signing, it is vital for organizations to leverage hardware security modules (HSMs). Keys stored on servers or other systems are too susceptible to unauthorized access and compromise. Storing keys in robust, tamper-evident HSMs can eliminate these risks.
Actors
Developer – Develops software and distribute it to the consumer for installation and use of the developed software.
Consumer – Consumes or uses the software distributed by the developer
Precondition
Code signing solution (software) should be integrated with CryptoBind HSM.
Flow
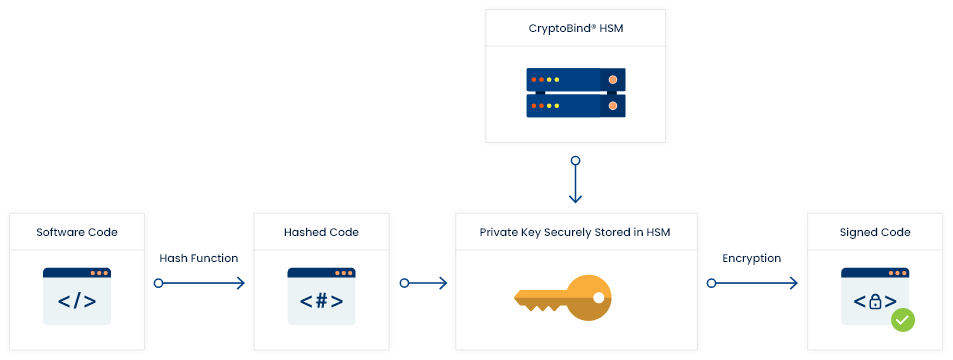
Code signing process flow is given below:
A. For developer
- First developer generates private-public key pair as per PKI mechanism and public key is sent to
trusted issuing body i.e. Certificate Authority (CA) - CA then verifies the developer’s authenticity and affixes public key with digitally signed
certificate. This ‘Code Signing Certificate’ is the developer’s proof that they are rightful owner
of the key. - Developer then hash the code.
- This hashed code is then encoded with private key, along with code signing certificate which
contains public key and identity of author. - The developer affix this block into the software to sign the code.
B. For Consumer
- When installation is prompted, the OS first confirms legitimacy of certificate and then uses a
public key to decrypt the digest. It is kept aside for comparison. - Next the OS uses the same hash function used by developer to create another hash from the code.
- The new hash is compared to the one which was kept aside.
- If they are identical, this proves that the code has not been tampered or altered since it was
distributed by developer. - If the OS does not recognize the certificate, it prompts user if they want to proceed ahead. User
may then decide if they want to terminate the installation or proceed.