Column level encryption is a type of database encryption method that allows user to select specific information or attributes to be encrypted instead of encrypting the entire database file.
Overview
Column level encryption is a type of database encryption method that allows user to select specific information or attributes to be encrypted instead of encrypting the entire database file. To understand why column level encryption is different from other encryption methods like file level encryption, disk encryption, and database encryption, a basic understanding of encryption is required.
Generally, when data are being collected and stored as records, those records will appearin a tabular format in rows in the database with each row logging specific attributes.Some data can be more sensitive than others, for example, data of birth, social security number, home address, etc., which can act as a personal identification. In order to ensure that these private information is transferred and stored securely, data goes through encryption, which is the process of encoding plaintext into ciphertext. Non-designated readers or receivers will not be able to read the data without the decryption key. Another example to illustrate this concept is, given a database stores client’s phone numbers. The set of phone numbers will appear to most readers as gibberish alphanumerical text with a mix of symbols, totally useless to those who do not have access privilege to view the data in plaintext (original form).
Because not all stored data are always sensitive and important, column level encryption was created to allow users the flexibility in choosing what sort of attributes should or should not be encrypted. This is to minimum performance disruption when executing crypto algorithms by moving data in and out of devices.
Application of J-Secure DB
Column level encryption does not store the same encryption key like table encryption does but rather separate keys for each column. This method minimizes the probability of unauthorized access. All keys are managed via J-KMS.

Advantages of column-level encryption
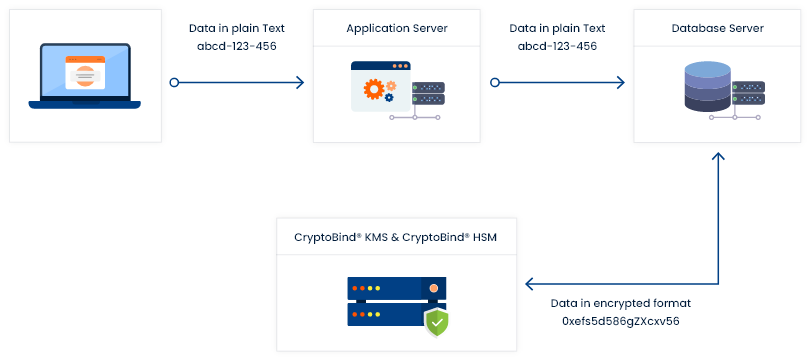
Below diagram explains how J-KMS & HSM can be configured with Database for data encryption. Here database APIs are configured with database to get master keys. Using these keys, data of particular columns can be encrypted.