CryptoBind KMS allows you to stay competitive by improving business efficiency, while reducing costs and risk.
Overview
Managing an increasing number of cryptographic keys across business applications is becoming ever more challenging, whereas manual, decentralized processes are costly and error prone, and demonstrating compliance is time consuming.
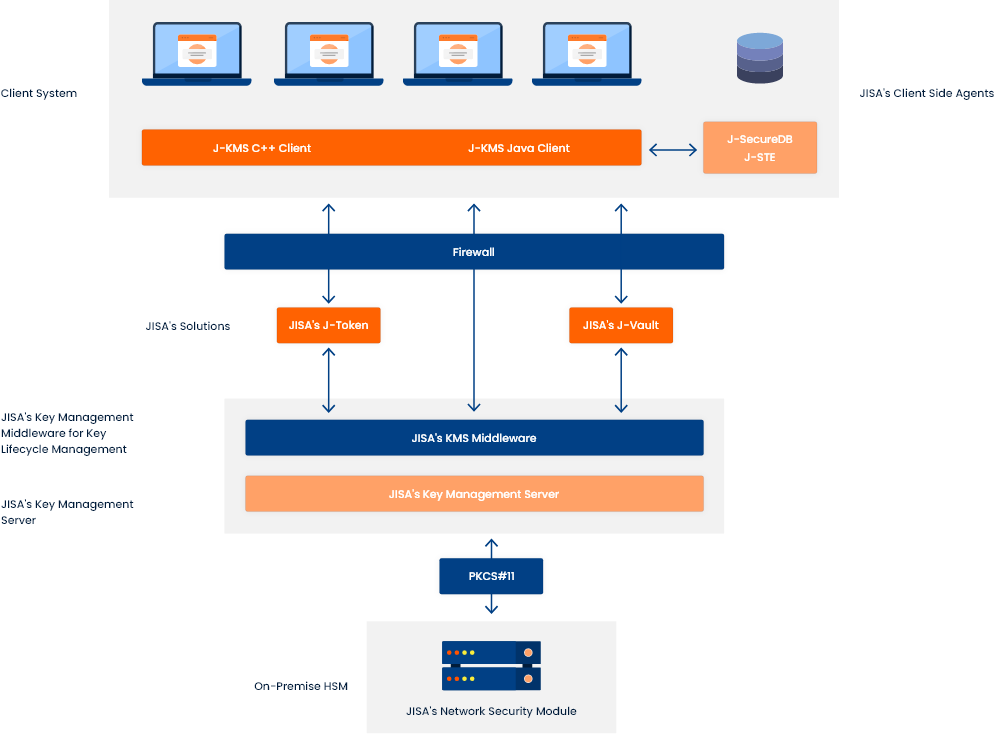
JISA’s CryptoBind KMS is a centralized key management system that delivers automated key updates and distribution to a broad range of applications. CryptoBind KMS manages the entire lifecycle of all keys (symmetric and asymmetric), supports robust business processes and allows you to confidently comply with and pass internal & external audits. Take control of cryptography and achieve compliance with centralized and automated application key management.
The top three challenges of key management are frequently cited as: lack of clear ownership of processes; lack of skilled personnel and the existence of isolated and fragmented systems.
CryptoBind KMS directly addresses all of these. It enforces specific roles and clear responsibilities for sets of keys; it frees staff from manual, repetitive tasks and allows them to concentrate on policy decisions; it can orchestrate the delivery of keys between disparate systems supporting standard key formats.
Protecting your business processes from internal and external attack requires the strongest protection for the roots-of-trust that underpin them. Demonstrating compliance with standards like PCI-DSS and GDPR is non-negotiable for many enterprises.
CryptoBind KMS allows you to stay competitive by improving business efficiency, while reducing costs and risk.
Functions of KMS

Benefits of CryptoBind KMS
Below listed are some benefits of CryptoBind KMS Key Management solution
CryptoBind KMS Use Case

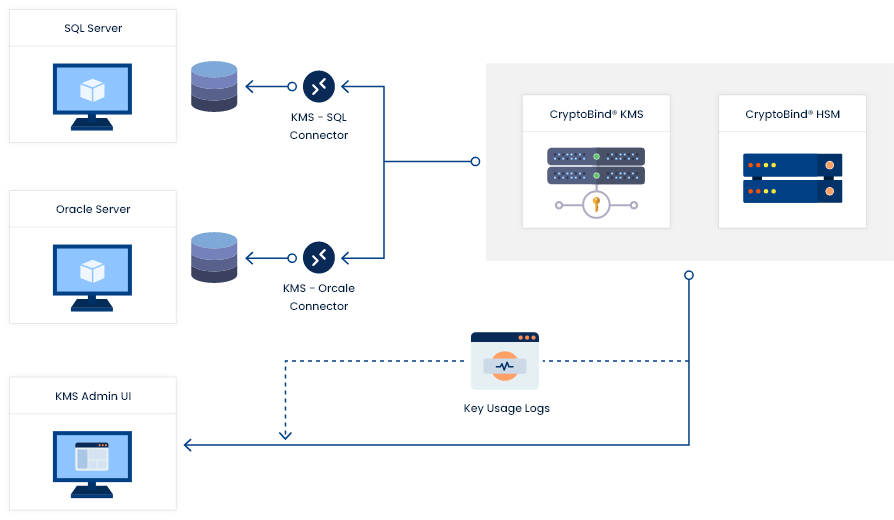
Data at Rest Encryption using CryptoBind KMS
Data at rest in information technology means inactive data that is stored physically in any digital form (e.g. databases, data warehouses, etc.). Data at rest is subject to threats from hackers and other malicious threats. To prevent this data from being accessed, modified or stolen, organizations will often employ security protection measures such as password protection, data encryption, or a combination of both. The security options used for this type of data are commonly referred to as data at rest encryption.
JISA CryptoBind KMS solution enables organizations to use native encryption of Database, Big data, Virtual Machines, etc. by provide KMIP based clients. In this CryptoBind KMS KMIP clients keys can be managed in synchronization with CryptoBind KMS KMIP Server.
JISA’s Solution